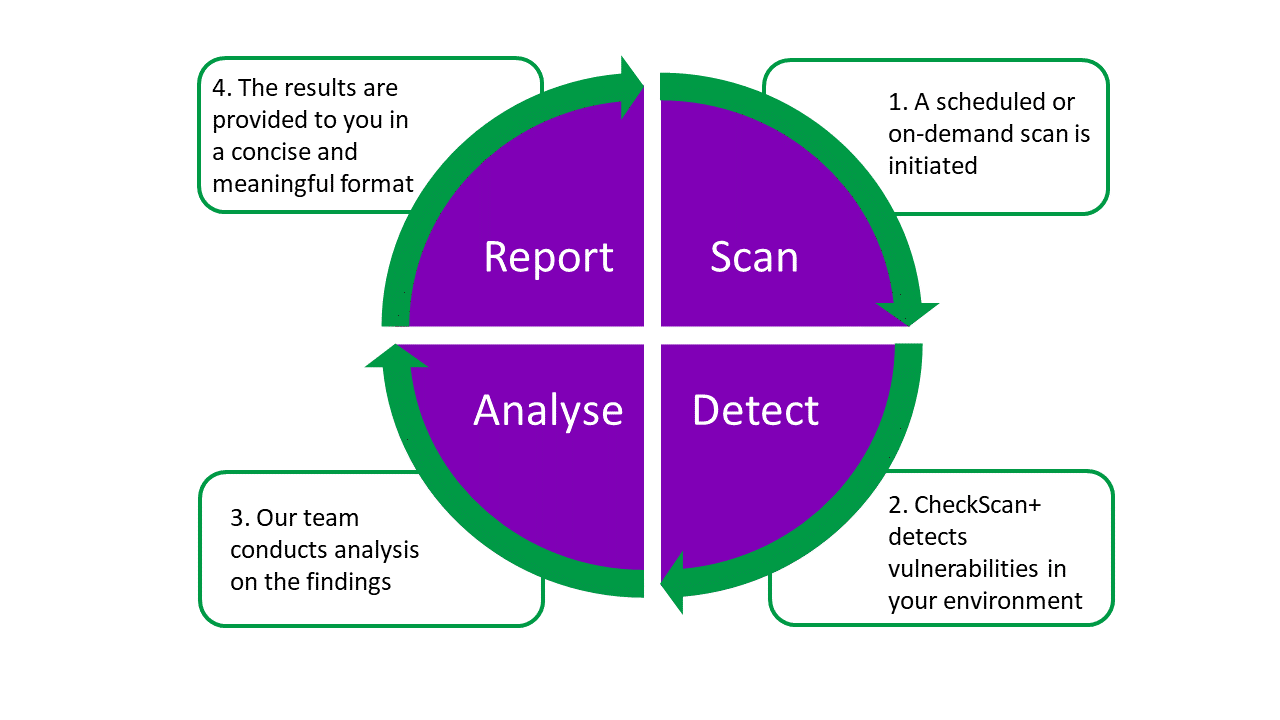
CheckScan+ is fully supported throughout the scanning engagement, from scoping and configuring your scans, to helping you understand and analyse your results. The service gives you access to technical support that is provided by our security consultants. We are available to explain the results in greater depth, remove false positives and provide remediation advice once initial testing is complete.
Basic Support included with all licenses
Through the Vulnerability Scanning platform we offer unlimited access to industry leading scanning technology. The SaaS portal allows you to configure and manage your own scans on a frequency that suits your business need.
Supported Feature Highlights included:
- Full access to unlimited Scans
- Administrative Support access via our helpdesk for basic queries such as FAQ’s
- Access to FAQ’s support page
- Notification of new updates/vulnerability discovery
Fully managed testing service
The CommSec managed Scanning Service combines industry leading application / infrastructure scanning technology and security expertise from our team of consultants. The hybrid service is designed for those who seek the assurance that consultant guided testing can provide.
The CommSec Managed service is fully supported throughout the scanning engagement, from scoping and configuring your scans, removal of false positive results and post scan support to help you understand and analyse your results.
Managed Service Feature Highlights
- CommSec’s complete management of the scanning process from Schedule, Configure and Manage.
- Receive sanitised reports that are free of false positives with each vulnerability verified through safe exploitation.
- 8/5 Technical Support, Remediation Advice provided via Security Consultants
- All Managed Service Scanning customers have full access to the SaaS tool outside the managed service. Provision your own scans on an unlimited frequency within your licence band in addition to your consultant guided scans.