A Complete Vulnerability Scanning Solution
Features at a glance:
- Unparalleled vulnerability coverage
- 24/7 vulnerability scanning
- Crawling modern complex applications
- Zero-day detection
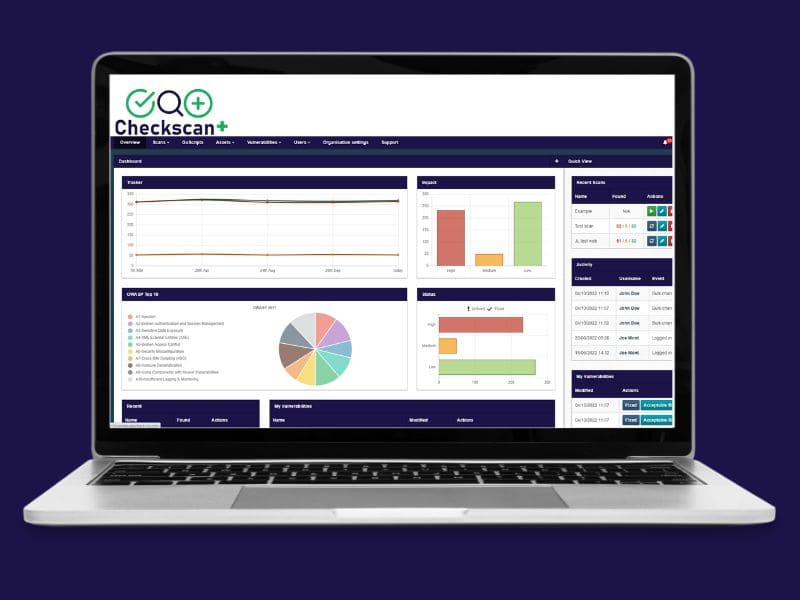
- Easy-to-use dashboard
A fully managed service based on sophisticated scanning technology designed by experienced penetration testers.
See why vulnerability scanning as a managed service can save you time, budget and increase your app or network security!
Delivered as a fully managed IT security service, CheckScan+ provides the capability to carry out regular scans to identify vulnerabilities in your applications and infrastructure (including AWS, Azure Cloud) that could quickly become a significant business risk. It can be deployed as a single scanning system or as part of a distributed scanning network, and it offers unparalleled detection rates, accuracy and scalability.
Vulnerabilities within web applications pose a significant threat to your organisation’s network security. A recent study revealed that cross site scripting (XSS) and SQL injection attacks have increased by more than 30%. In addition, almost half of organisations recently surveyed reported SQL injections as the most serious attacks they have experienced in the past two years. CheckScan+ can identify all known web application vulnerabilities and provide exploit capabilities to demonstrate their impact and eradicate false positives.
Web application vulnerabilities are not the only threat to your network perimeter, including the Cloud. Unpatched software, configuration weaknesses and software vulnerabilities also need to be managed effectively. CheckScan+ includes a vulnerability assessment module to perform vulnerability scans across your external network infrastructure.
The CheckScan+ vulnerability management platform enables the team in CommSec, working with you the customer, to manage the vulnerabilities discovered across the business in a variety of ways. CommSec have designed the vulnerability management platform to be completely customisable. CheckScan+ has been specifically designed to enable CommSec to work with you to understand and prioritise the vulnerabilities that matter most to you, and we customise the service to those priorities.
Traditional penetration testing is an important part of security management. However, this testing can be expensive and only shows results from a point in time. By continuously scanning your environment, vulnerabilities can be spotted and remediated quickly, instead of waiting for an annual penetration test to find them.
Continuous security testing is required to give visibility and a single pane of glass to track your security health over time.
Accurate and efficient component discovery (crawling) is commonly cited as one of the key challenges when performing an automated web application assessment. Many existing web application scanners rely on parsing web pages in order to discover application components (e.g. links and forms). This approach is no longer effective when testing modern web 2.0 based applications. Components generated at runtime using JavaScript, Flash or Silverlight components will remain invisible to traditional discovery techniques. The CheckScan+ scanning engine employs two integrated crawling technologies to overcome this challenge. Our HTTP/HTML based crawler is used to discover components quickly and to identify hidden components through forced browsing. A second integrated crawling engine then executes web pages in the same way a normal browser would. Any embedded scripts or components are then able to run as intended whilst allowing full visibility to the discovery engine. If a modern web browser such as Google Chrome can access the application, our scanning software can crawl it.
CheckScan+ has been designed from the ground up to offer the most sophisticated scanning engine available. By working closely with industry leading penetration testers, each scanning module has been designed to maximise detection accuracy whilst minimising false positives.
CheckScan+ incorporates dynamic fuzzing technology whereby arbitrary protocol structures treated blindly by other scanners as opaque single inputs are broken down accurately into their true and deeper attack surface. For example, cookie values often encode multiple sub parameters using bespoke serialisation encodings (e.g. “the_cookie=1234|65[a=b;c=[1,2,3]]”), and so vulnerable server-side code paths are frequently missed using traditional fuzzing technology.
A false positive is where a vulnerability scanner indicates there is a vulnerability when in fact there isn’t one. Sorting through scanner results to determine which reported issues are real and which are false positive is a time-consuming process. To eliminate false positives, and to provide proof of concept evidence, CheckScan+ employs safe custom exploit techniques to actively confirm discovered vulnerabilities.
With CheckScan+ you can download custom filtered results and view via HTML, Docx or CSV. CheckScan+ includes a simple JSON data API for retrieving, aggregating, processing and reporting raw vulnerability data for use in third party applications.
CheckScan+ allows you to create multiple (unlimited) user accounts to allow team collaboration. The system includes workflow management allowing you to assign and prioritise each vulnerability’s remediation to nominated members of the CommSec technical team who are managing your environment, or to nominated members of your own technical team if you wish.
Complex authentication schemes are supported when we are supplied with the minimal information, such as a username and password pair. Optionally, a login URL may be provided to direct the scanner where to use the credentials and for scenarios such as single sign-on. The scanner may easily be adapted to support bespoke authentication schemes that require non-standard credentials or processes.
CommSec can provide a comprehensive vulnerability assessment and analysis against remote hosts to determine if a misconfiguration exists that could allow an attack to get behind the application and into sensitive data.
A member of our team will get back to you as soon as possible. They will find a suitable time to speak with you, answer any questions you have and help find the perfect solution to suit your requirements.